Nginx支持TLS1.3,及0-RTT测试。
软件版本
需要将openssl编译到nginx中, nginx -V命令查看编译信息。
nginx/1.20.2
openssl-1.1.1w
nginx.conf
# 为防止重放除了GET、HEAD请求全都返回HTTP状态码425(浏览器会默认重发1次请求)
map $ssl_early_data$request_method $early_data_non_idempotent {
"1POST" 1;
"1PUT" 1;
"1DELETE" 1;
"1PATCH" 1;
"1OPTIONS" 0;
"1GET" 0;
"1HEAD" 0;
default 0;
}
server {
listen 443 ssl http2;
server_name www.iarno.cn;
server_tokens off;
keepalive_timeout 5;
......省略
include /usr/local/nginx/conf/http/general/ssl.conf;
ssl_certificate /usr/local/nginx/ssl/www.iarno.cn.crt;
ssl_certificate_key /usr/local/nginx/ssl/www.iarno.cn.key;
......省略
access_log logs/https.log combinedio buffer=4k;
error_log logs/https_error.log;
location / {
if ($early_data_non_idempotent) {
return 425; # Non-idempotent operations return 425 Too Early
}
include /usr/local/nginx/conf/https_proxy.conf;
......省略
}
}
ssl.conf
ssl_stapling on;
ssl_session_tickets on; # 是否复用sesssion ticket, openssl发送early data数据后每次会新生成session
ssl_early_data on; # 开发early data (0-RTT)
ssl_session_ticket_key /usr/local/nginx/conf/ssl_session_ticket.key;
ssl_session_timeout 10m; # early_data过期时间
ssl_protocols TLSv1 TLSv1.1 TLSv1.2 TLSv1.3;
ssl_ciphers 'TLS_AES_256_GCM_SHA384:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_128_GCM_SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-DSS-AES128-GCM-SHA256:kEDH+AESGCM:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA384:ECDHE-RSA-AES256-SHA:ECDHE-ECDSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-DSS-AES128-SHA256:DHE-RSA-AES256-SHA256:DHE-DSS-AES256-SHA:DHE-RSA-AES256-SHA:ECDHE-RSA-DES-CBC3-SHA:ECDHE-ECDSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:AES:DES-CBC3-SHA:HIGH:!aNULL:!eNULL:!EXPORT:!DES:!RC4:!MD5:!PSK:!aECDH:!EDH-DSS-DES-CBC3-SHA:!EDH-RSA-DES-CBC3-SHA:!KRB5-DES-CBC3-SHA';
ssl_prefer_server_ciphers on;
https_proxy.conf
proxy_set_header Connection "";
proxy_set_header Host $server_name;
proxy_set_header Early-Data $ssl_early_data; # 设置early data标识
proxy_connect_timeout 5s;
proxy_send_timeout 5s;
proxy_read_timeout 5s;
TLS1.3验证
https://www.ssllabs.com/ssltest/analyze.html?d=www.taobao.com&latest
https://github.com/drwetter/testssl.sh
➜ testssl.sh git:(3.2) ✗ ./testssl.sh -p www.taobao.com
###########################################################
testssl.sh 3.2rc3 from https://testssl.sh/dev/
(1dbd9b8 2024-07-18 09:09:13)
This program is free software. Distribution and
modification under GPLv2 permitted.
USAGE w/o ANY WARRANTY. USE IT AT YOUR OWN RISK!
Please file bugs @ https://testssl.sh/bugs/
###########################################################
Using "OpenSSL 1.0.2-bad (1.0.2k-dev)" [~183 ciphers]
xxxx:./bin/openssl.Darwin.x86_64
(built: "Sep 3 14:46:36 2022", platform: "darwin64-x86_64-cc")
Testing all IPv4 addresses (port 443): 119.188.122.194 119.188.122.195
-----------------------------------------------------------------------------------------------
Start 2024-07-25 15:59:51 -->> 119.188.122.194:443 (www.taobao.com) <<--
Further IP addresses: 119.188.122.195 2408:8719:64:54:3::3da 2408:8719:64:54:3::3db
rDNS (119.188.122.194): --
Service detected: HTTP
Testing protocols via sockets except NPN+ALPN
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered (deprecated)
TLS 1.1 offered (deprecated)
TLS 1.2 offered (OK)
TLS 1.3 offered (OK): final
NPN/SPDY h2, http/1.1 (advertised)
ALPN/HTTP2 h2, http/1.1 (offered)
Done 2024-07-25 15:59:59 [0014s] -->> 119.188.122.194:443 (www.taobao.com) <<--
-----------------------------------------------------------------------------------------------
Start 2024-07-25 15:59:59 -->> 119.188.122.195:443 (www.taobao.com) <<--
Further IP addresses: 119.188.122.194 2408:8719:64:54:3::3da 2408:8719:64:54:3::3db
rDNS (119.188.122.195): --
Service detected: HTTP
Testing protocols via sockets except NPN+ALPN
SSLv2 not offered (OK)
SSLv3 not offered (OK)
TLS 1 offered (deprecated)
TLS 1.1 offered (deprecated)
TLS 1.2 offered (OK)
TLS 1.3 offered (OK): final
NPN/SPDY h2, http/1.1 (advertised)
ALPN/HTTP2 h2, http/1.1 (offered)
Done 2024-07-25 16:00:08 [0023s] -->> 119.188.122.195:443 (www.taobao.com) <<--
-----------------------------------------------------------------------------------------------
Done testing now all IP addresses (on port 443): 119.188.122.194 119.188.122.195
Early Data(0-RTT)验证
openssl验证
# 第一步
➜ ~ openssl s_client -connect www.taobao.com:443 -tls1_3 -sess_out session.pem
Connecting to 119.188.122.195
CONNECTED(00000006)
depth=2 C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA
verify return:1
depth=1 C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G3
verify return:1
depth=0 C=CN, ST=ZheJiang, L=HangZhou, O=Alibaba (China) Technology Co., Ltd., CN=*.tbcdn.cn
verify return:1
---
Certificate chain
0 s:C=CN, ST=ZheJiang, L=HangZhou, O=Alibaba (China) Technology Co., Ltd., CN=*.tbcdn.cn
i:C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G3
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Jun 19 09:06:02 2024 GMT; NotAfter: Jul 21 09:06:01 2025 GMT
1 s:C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G3
i:C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA
a:PKEY: rsaEncryption, 2048 (bit); sigalg: RSA-SHA256
v:NotBefore: Sep 4 00:00:00 2015 GMT; NotAfter: Sep 4 00:00:00 2025 GMT
---
Server certificate
-----BEGIN CERTIFICATE-----
......省略
-----END CERTIFICATE-----
subject=C=CN, ST=ZheJiang, L=HangZhou, O=Alibaba (China) Technology Co., Ltd., CN=*.tbcdn.cn
issuer=C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G3
---
No client certificate CA names sent
Peer signing digest: SHA256
Peer signature type: RSA-PSS
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 4600 bytes and written 332 bytes
Verification: OK
---
New, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
This TLS version forbids renegotiation.
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was not sent
Verify return code: 0 (ok)
---
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
......省略
Start Time: 1721893373
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
Max Early Data: 16384
---
read R BLOCK
---
Post-Handshake New Session Ticket arrived:
SSL-Session:
......省略
Start Time: 1721893373
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
Max Early Data: 16384
---
read R BLOCK
closed
# 第二步
➜ ~ echo -e "GET / HTTP/1.1\r\nHost: www.taobao.com\r\n\r\n" > early_data.txt
➜ ~
# 第三步
➜ ~ openssl s_client -connect www.taobao.com:443 -tls1_3 -sess_in session.pem -early_data early_data.txt
Connecting to 119.188.122.194
CONNECTED(00000006)
---
Server certificate
-----BEGIN CERTIFICATE-----
......省略
-----END CERTIFICATE-----
subject=C=CN, ST=ZheJiang, L=HangZhou, O=Alibaba (China) Technology Co., Ltd., CN=*.tbcdn.cn
issuer=C=BE, O=GlobalSign nv-sa, CN=GlobalSign Organization Validation CA - SHA256 - G3
---
No client certificate CA names sent
Server Temp Key: X25519, 253 bits
---
SSL handshake has read 249 bytes and written 728 bytes
Verification: OK
---
Reused, TLSv1.3, Cipher is TLS_AES_256_GCM_SHA384
Server public key is 2048 bit
This TLS version forbids renegotiation.
Compression: NONE
Expansion: NONE
No ALPN negotiated
Early data was accepted
Verify return code: 0 (ok)
---
HTTP/1.1 200 OK
Server: Tengine
Content-Type: text/html; charset=utf-8
Transfer-Encoding: chunked
Connection: keep-alive
Date: Thu, 25 Jul 2024 07:44:31 GMT
x-server-id: 28c3d6b2523ca52c32ad72931842b19a621c8cdfdfbcaabcd5562acb7211986218860f5b9ea54579
x-air-hostname: air-ual033043202123.center.na610
x-air-trace-id: 7b06169817218934709936299e
Cache-Control: max-age=0, s-maxage=118
x-node: 9c0775731c8445d0bdf09cefd3e4bbf3
x-eagleeye-id: 7b06169817218934709936299e
x-retmsg: ok
x-content-type: text/html; charset=utf-8
streaming-parser: open
x-retcode: SUCCESS
x-readtime: 178
x-via: cn5026.l1, cache13.cn5026, l2nu16-1.l2, cache21.l2nu16-1, wormholesource033102016177.center.na610
x-air-source: proxy
x-xss-protection: 1; mode=block
Strict-Transport-Security: max-age=31536000
Ups-Target-Key: air-ual.vipserver
X-protocol: HTTP/1.1
EagleEye-TraceId: 7b06169817218934709936299e
s-brt: 181
Via: cache21.l2nu16-1[212,162,304-0,C], cache14.l2nu16-1[167,0], cache4.cn6806[0,0,200-0,H], cache20.cn6806[1,0]
Vary: Accept-Encoding
Vary: Ali-Detector-Type, X-Host, Accept-Encoding, Origin
etag: W/"bf15d-yE/eVpg40kEzpV7XQBu+BBmxaWc"
Age: 54
Ali-Swift-Global-Savetime: 1721893471
X-Cache: HIT TCP_MEM_HIT dirn:-2:-2
X-Swift-SaveTime: Thu, 25 Jul 2024 07:44:31 GMT
X-Swift-CacheTime: 118
x-air-pt: pt0
Timing-Allow-Origin: *
EagleId: 77bc7a9917218935251046825e
7a84
......... 页面源代码
0
---
Post-Handshake New Session Ticket arrived: # 如果nginx配置ssl_session_tickets=off才会有次内容,每次会新生成session
SSL-Session:
......省略
Start Time: 1721893527
Timeout : 7200 (sec)
Verify return code: 0 (ok)
Extended master secret: no
Max Early Data: 16384
---
read R BLOCK
C097125AF87F0000:error:0A000126:SSL routines::unexpected eof while reading:ssl/record/rec_layer_s3.c:692:
Chrome浏览器验证
chrome://flags/
开启TLS1.3 Early Data,默认为关闭状态。
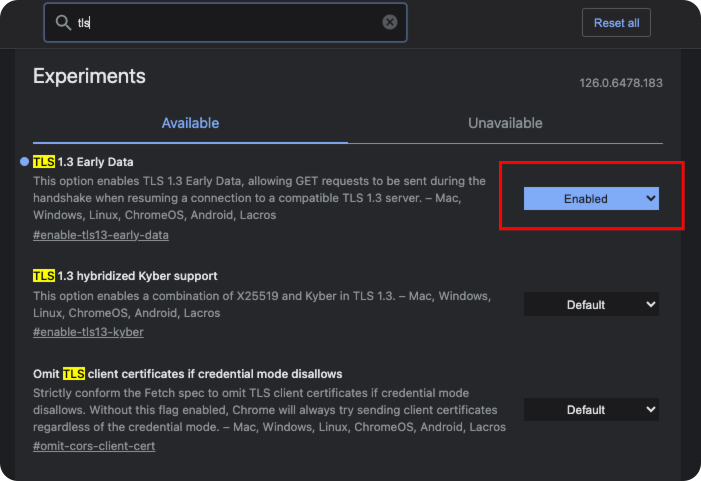
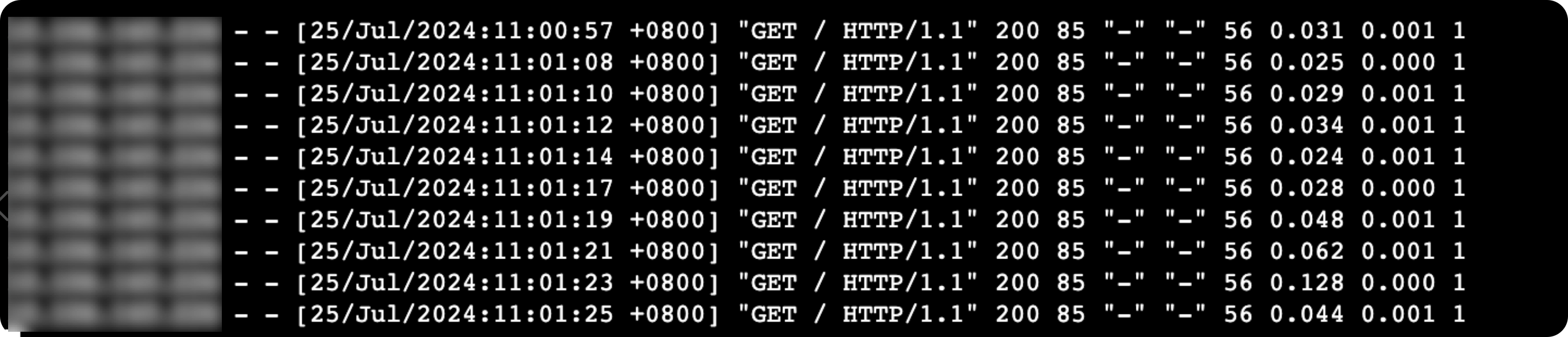
修改nginx日志格式
log_format combinedio '$remote_addr - $remote_user [$time_local] '
'"$request" $status $body_bytes_sent '
'"$http_referer" "$http_user_agent" $request_length $request_time $upstream_response_time $ssl_early_data'; # $ssl_early_data 访问日志新增early data标识
参考
https://blog.csdn.net/SkyChaserYu/article/details/105840504
